About the Customer
Botgate is a Estonia based startup software company developing conversational bot applications and platforms. The application is a plug & play (no-code), fully customizable, conversational marketing and sales AI bot focused on boosting B2B & B2C lead capture, shrinking sales cycle with personalized experiences, and engaging customers 24/7.
With Botgate AI, conversations can be started with future customers now, on their terms — not days later. There is overuse Botgate AI today to generate more revenue, shrink sales cycles, and make buying easy. Botgate’s mission is to use conversations to make business buying frictionless, more enjoyable, and more human.
Customer Challenge
Botgate’s goal was to revolutionize customer infrastructure and deployment strategy within their Amazon Elastic Kubernetes Service (EKS) environment. The challenge involved transitioning from a traditional setup to a more efficient, secure, and scalable system. The existing framework struggled with inefficient infrastructure deployment, security vulnerabilities in container image deployment, and suboptimal performance for AI workloads. Additionally, there were significant gaps in their monitoring and logging capabilities, coupled with inadequate network management. The firm aimed to employ Terraform for infrastructure deployment, enhance security measures for container images, optimize Kubernetes for AI workloads, and improve overall monitoring and network management. By leveraging advanced tools like Terraform, New Relic, and AWS CloudWatch, and adopting best practices in Kubernetes configurations and load balancing, the firm envisioned a robust, agile, and secure environment. This overhaul was critical to enhance their application performance, ensure tighter security, and facilitate efficient resource management in their AWS EKS setup.
How the solution was deployed to meet the challenge
The delivery of the solution was planned in two main phases: discovery and implementation.
The findings were documented with architectural recommendations during the discovery phase. Implementation phase as the name implies, was the phase when the agreed solution was deployed.
The solution’s components were:
- Detailed analysis of the current architecture of Botgate.AI environment. Documentation of current to be architectures of testing and production environments with migration strategy and planning details.
- Development of Terraform scripts of current production environment and testing the scripts.
- Update developed Terraform script to comply with the hardware requirements of the testing environment.
- Provision the AWS services by running developed Terraform script for testing environment and restoring the test database from its backup.
- Provision the AWS services with running developed Terraform script for new production environment that will be the copy of the current environment and restoring the test database from its latest backup. Redirecting the web traffic to new account.
- Integrate New Relic and CloudWatch with EKS.
- Assist to change configurations in Jenkins for new production environment.
Third party applications or solutions used
Jenkins: It’s running for the deployment of Kubernetes configurations and other automated processes. Hosted on an EC2 instance within the company’s AWS environment, it is facilitating efficient and automated workflows in the cloud infrastructure.
Azure Repos: Azure Repos serves as the preferred version control system for storing Terraform scripts and Kubernetes configuration files. This choice allows for effective management of source code and enhances collaborative development practices.
Terraform: The company uses Terraform for infrastructure as code (IaC) to automate the deployment of their cloud infrastructure on AWS. This tool enables them to efficiently manage and version their infrastructure setup, with Terraform scripts stored in a version control system for better collaboration and tracking.
Dockle: As a container image scanning tool, Dockle is integrated into the CI/CD pipeline to identify security vulnerabilities in container images. It scans images during the build phase and at deployment, ensuring a high level of security for the EKS cluster.
Istio: Deployed via Helm, Istio is the chosen service mesh solution for the Kubernetes environment. It manages the configuration of the service mesh and facilitates dynamic service discovery and routing, enhancing network efficiency and security.
OpenVPN: It is used for SSH Connection to AWS environment and Jenkins Dashboard access. It is installed on two EC2 instances for both test and production environment.
MongoDB: MongoDB is running in a replica set with 3 EC2 nodes.
New Relic: It is integrated with EKS cluster to monitor cluster resources and applications running.
AWS Services used as part of the solution
EKS is used for Kubernetes cluster management.
ELB is used for allowing access to the services exposed in EKS.
ElastiCache is used for applications deployed in EKS.
ECR is used for storing application container images.
S3 is used for storing Terraform state file, MongoDB dump backups and CDN as source. CloudFront: is used for CDN.
IAM is used for managing users and secrets in AWS.
Lambda is used for triggering SNS
EC2 is used as EKS nodes, MongoDB, Jenkins and OpenVPN
EBS Is used as an intermediate device for Dropbox synchronization to S3.
VPC is used for defining virtual network for the workloads in AWS account.
Secrets Manager is used for storing sensitive credentials.
CloudWatch is used for collecting metrics, logs and creating alarms. OpenSearch: is used for applications deployed in EKS.
EFS is used as a destination for MongoDB backups.
AWS Backup is used for taking backups of MongoDB and Jenkins instances.
Outcomes
Following the project delivery, Botgate AWS setup featured Amazon EKS for efficient container orchestration, MongoDB on EC2 instances for DB services and Amazon ElastiCache for enhanced performance. Jenkins on EC2 streamlines CI/CD processes with ELB managing traffic distribution. Monitoring is handled by Amazon CloudWatch and security and secret management through AWS Secret Manager and OpenVPN. As a result, all these resulting secure, scalable, and efficient cloud environments.
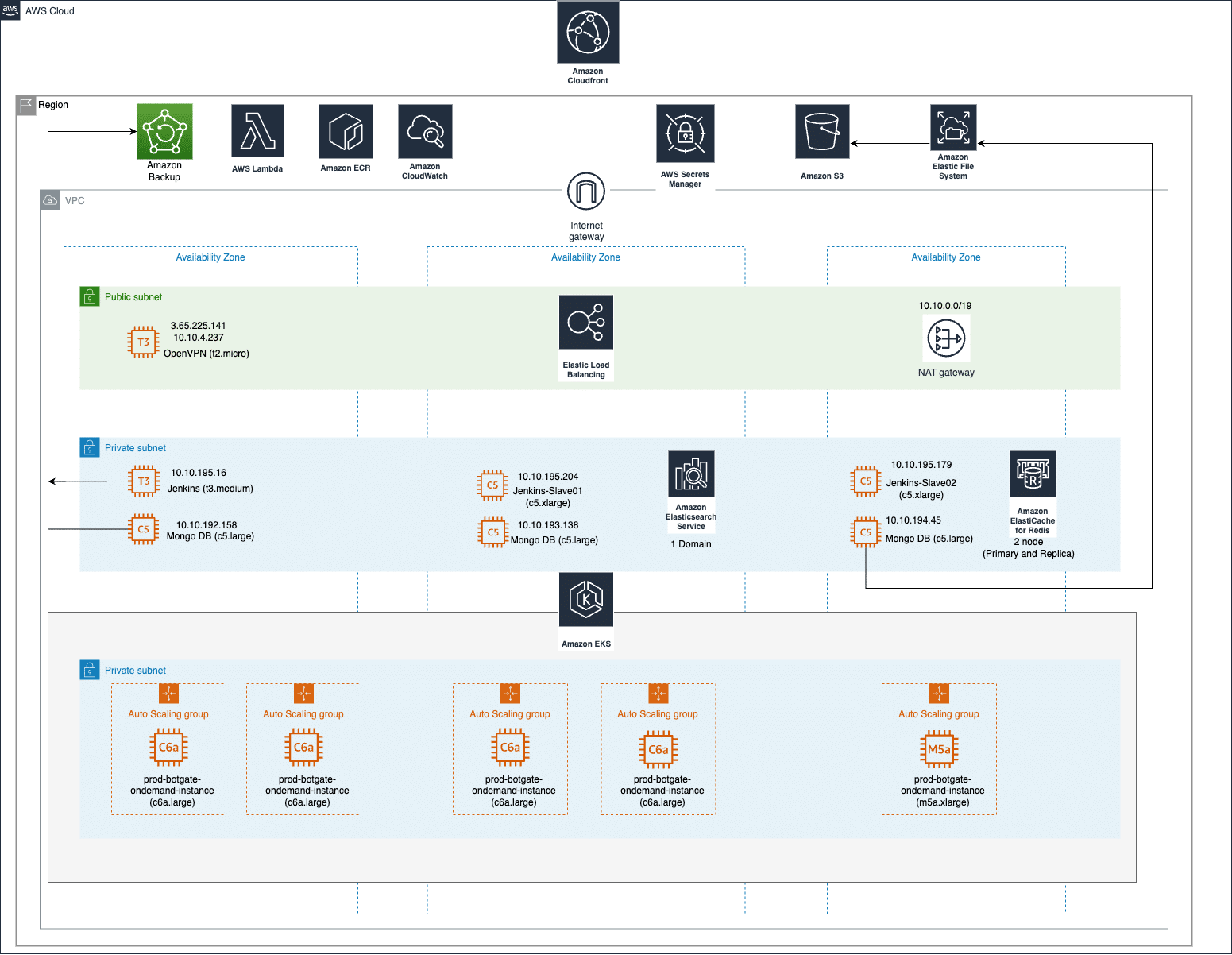
Architecture Diagrams of the specific customer deployment
Technical Requirements
High level requirements were defined as:
- Implementation of Amazon EKS for managing containerized applications with auto-scaling capabilities to ensure efficient load management and high availability.
- Deployment of EC2 instances within auto-scaling groups in private subnets to host application, optimizing for performance & cost.
- Use of NAT GWs in each AZ to enable instances in private subnet to connect to the internet or AWS services while preventing incoming internet traffic.
- Configuration of an ELB to distribute incoming application traffic across multiple EC2 instances, improving fault tolerance and scalability.
- Implementing Jenkins on EC2 instances for automating CI/CD pipeline to ensure reliable application deployment.
- Deployment of Amazon CloudFront as CDN to cache content and reduce latency. -Use of Route53 for reliable DNS web services.
- Integration of ElastiCache for Redis to enhance application performance through in-memory data caching and storage.
- Configuration of EFS for scalable file storage to be easily accessible by EC2 instances and other AWS services.
- Implementation of OpenVPN access server in a public subnet to provide secure VPN access for remote management and administration.
- Deployment of MongoDB on EC2 instances within private subnets for database services, ensuring data persistence and security.
- Implementation of MongoDB Dump Backups on the S3 Buckets. Used the Lambda for triggering the Backup Scripts and SNS Notification.
Client Case Studies
We deliver solutions using our extensive knowledge and more than 10 years of cloud transformation experience.