Ensuring Robust Cloud Security with AWS
Ensuring Robust Cloud Security with AWS
Regardless of whether your business is considering a cloud migration from on-premises or has been thriving in the cloud for years, security remains a top priority. The simplicity with which AWS allows the expansion and integration of new services also brings a persistent risk of overlooking important security measures. A true security system depends not just on state-of-the-art technology, but also on informed personnel and refined processes.
Any one of these aspects can make you more vulnerable to security threats. As your enterprise grows and the technology landscape rapidly evolves, maintaining an awareness of new tools, capabilities, and threats is essential to avoid introducing vulnerabilities. Amazon Web Services (AWS) offers an extensive suite of services to enhance your security strategy, and with the support of a seasoned AWS Partner like Commencis, you can establish a robust and adaptable security foundation in the cloud.
Embracing the AWS Shared Responsibility Model
AWS operates on a Shared Responsibility Model, which is fundamental to understanding cloud security. AWS secures the cloud infrastructure, including hardware, software, networking, and facilities that run AWS Cloud services. On the other hand, customers are responsible for securing their data, applications, and other resources they run in the cloud. This model underscores the need for customers to be vigilant and proactive in securing their part of the cloud.
In-Depth Defense with Identity and Access Management (IAM)
A cornerstone of AWS security is a sophisticated Identity and Access Management (IAM) system. IAM is your first line of defense, allowing you to meticulously control access to AWS services and resources. The principle of least privilege is key here, meaning users are given only the permissions they need to perform their jobs. This minimizes the risk of an attacker gaining access to sensitive resources through a compromised account.
Adding another layer of security, Multi-Factor Authentication (MFA) is essential, especially for administrative accounts or those with access to sensitive data. MFA requires users to provide two or more verification factors to gain access, adding a significant barrier to unauthorized access.

Data Encryption: Safeguarding Data at Rest and In-Transit
AWS advocates a comprehensive encryption strategy. Key Management Service is an integral part of AWS’s encryption and security architecture, especially in the context of safeguarding data at rest. AWS KMS (Key Management Service) is a managed service that makes it easy for you to create and control the encryption keys used to encrypt your data. The service is designed to help you secure your data at rest across AWS services that integrate with KMS, such as Amazon S3 (Simple Storage Service), EBS (Elastic Block Store), and RDS (Relational Database Service), among others. When it comes to data in transit, AWS enables encryption via TLS across all its services, ensuring that your data is not intercepted when moving from one location to another.
Proactive Surveillance with AWS Control Tower, Amazon GuardDuty, AWS CloudTrail, and AWS Security Hub
To maintain a strong security posture, AWS offers several services that help monitor and manage security and compliance.
AWS Control Tower automates the setup of a baseline environment based on AWS best practices. It provides a way to monitor your AWS environment with guardrails that ensure compliance with policies and detect policy violations.
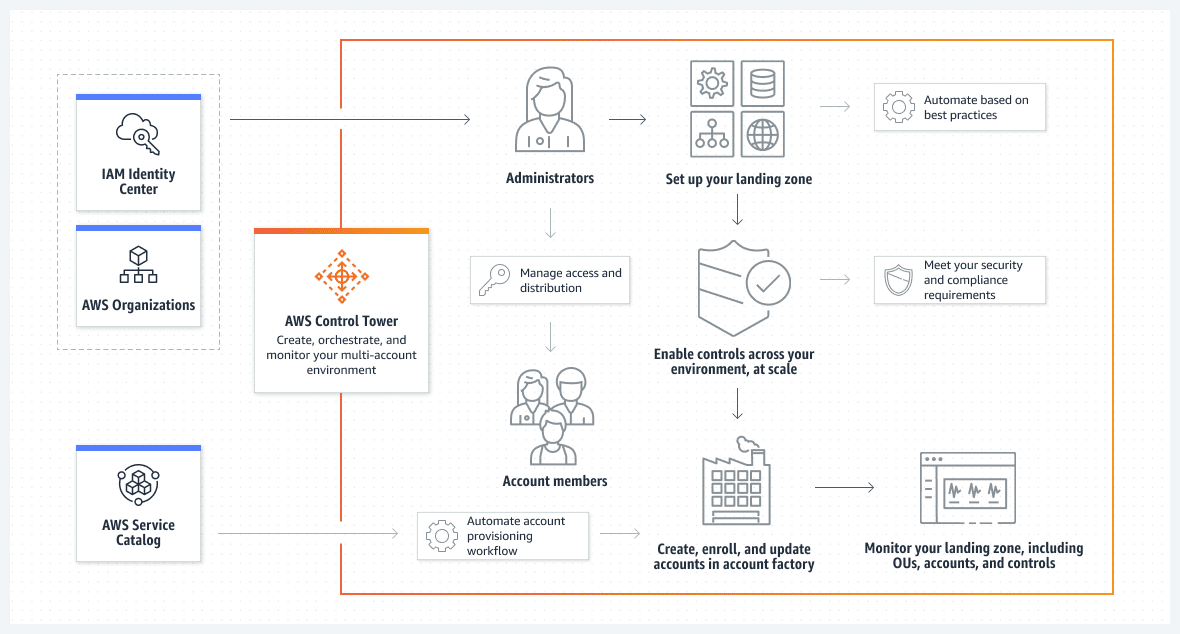
Source: AWS Control Tower
Amazon GuardDuty is a threat detection service that continuously monitors malicious activity and unauthorized behavior. It uses machine learning, anomaly detection, and integrated threat intelligence to identify and prioritize potential threats.
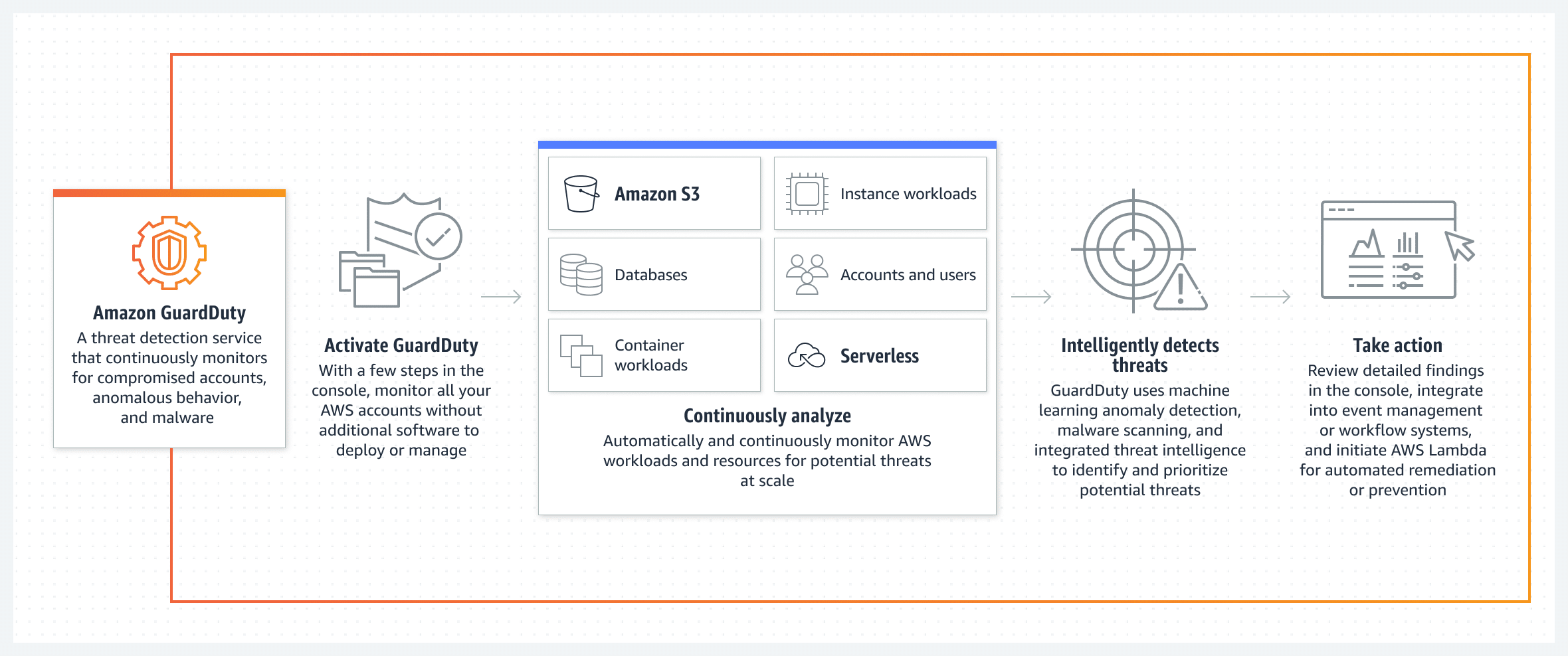
Source: Amazon GuardDuty
AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account. It logs all actions taken by a user, role, or AWS service. This is essential for understanding and investigating what occurred in your AWS environment.
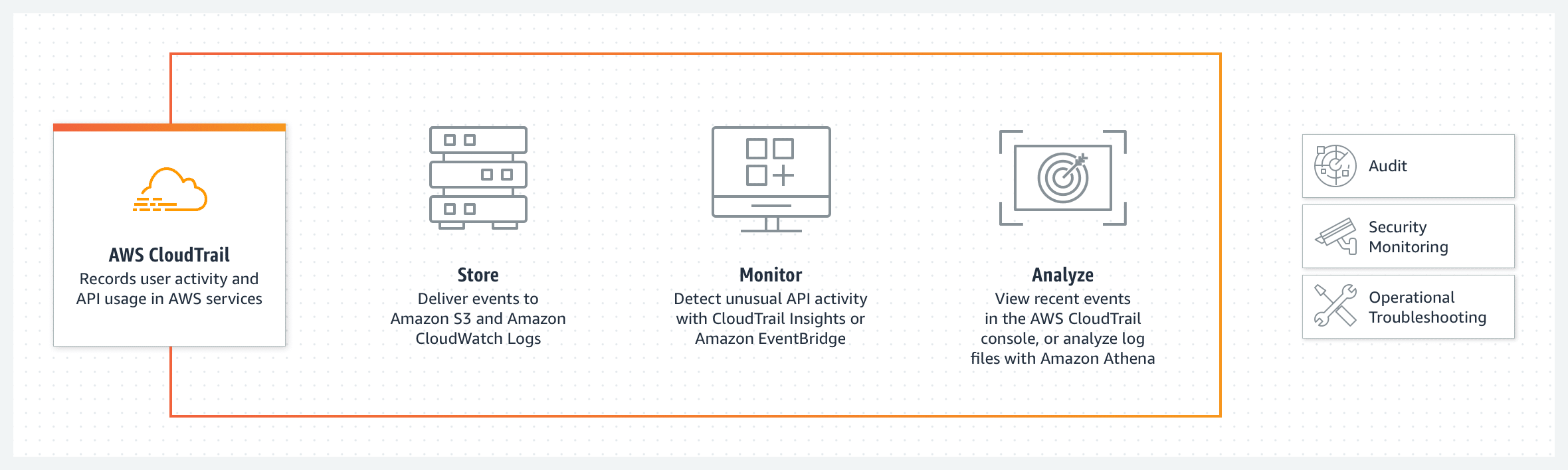
Source: AWS CloudTrail
AWS Security Hub gives you a comprehensive view of your high-priority security alerts and compliance status across AWS accounts. It aggregates, organizes, and prioritizes alerts and findings from AWS services like Amazon GuardDuty, Amazon Inspector, and Amazon Macie, as well as from AWS Partner solutions.
By integrating these services into your security strategy, you can ensure continuous compliance, quickly detect, and respond to potential threats, and maintain a rigorous audit trail for your cloud activities.
Key Takeaways
Security in the cloud is an ongoing process. By understanding and utilizing the tools and services provided by AWS, you can build a robust security environment that not only protects your resources but also adapts to new threats as they arise. The combination of strong access control, data encryption, network security configurations, and continuous monitoring will place you in a strong position to secure your AWS cloud infrastructure.
In addition to these tech strategies, it’s important to ensure everyone in your company knows how important security is. When your team knows what to watch out for and how to handle sensitive information, they help keep your cloud environment safe. AWS keeps updating and adding new security features, so staying in the loop can strengthen your defenses. Also, taking advantage of AWS’s security training can give your team the knowledge they need to protect your systems better.
Commencis is an AWS Advanced Consulting Partner that helps organizations develop Cloud Native Applications. Commencis has a deep understanding of the approach and can help organizations apply it in a way that meets their specific needs. Contact our cloud experts to enable cloud workload efficiency in your business.
Reading Time: 4 minutes
Don’t miss out the latestCommencis Thoughts and News.




