OWASP Top 10 Mobile Risks: A Must-Know Guide for QA Engineers
As QA professionals, understanding and addressing security risks is an important part of building better software. Mobile apps are a big target for security threats, so it’s not enough to check if they work correctly. QA teams need to think about security too. By asking the right questions and doing detailed testing, we can help ensure the apps we work on are not only high-quality but also safe for users. In this blog, I’ll talk about some of the OWASP Top 10 Mobile Risks and share how QA teams can help find and fix these issues. Whether you’re new to security testing or already know a bit about it, this guide will give you practical tips to make mobile apps safer.
What is OWASP?
The Open Worldwide Application Security Project (OWASP) is a nonprofit foundation dedicated to improving software security. Its Mobile Top 10 Risks list highlights the most significant security threats to mobile applications.
While the full list contains essential insights, I’ll focus on a few key risks that I find particularly critical for QA teams to address.
Why Considering Security Risks is Important for QA
- Maintaining Reputation: By addressing security risks at the early stage of development, QA engineers contribute to building and maintaining trust among users, customers, and stakeholders.
- Identifying Vulnerabilities Early & Preventing Financial Loss: Addressing security concerns early in the development process is more cost-effective than fixing them later. QA engineers can contribute to the identification of vulnerabilities during the testing phase, helping developers address issues before they reach production.
- Adopting a Proactive Approach: QA engineers can contribute by staying informed about the latest security trends, incorporating security testing into their processes, and promoting a culture of security awareness within the development team.
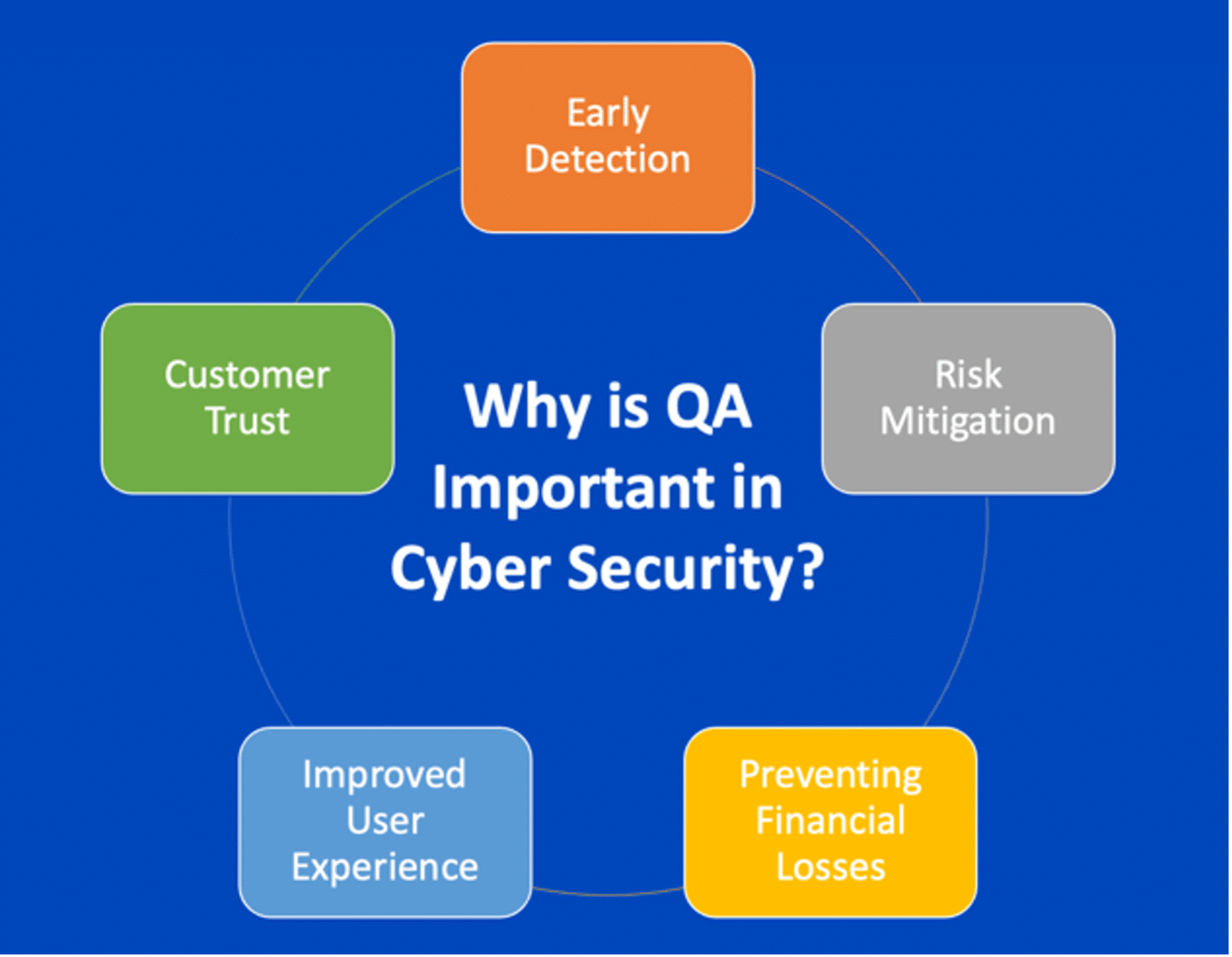
Key OWASP Mobile Risks to Address
Improper Credential Usage: Failure to securely manage credentials throughout their lifecycle, from creation to storage and transmission. Includes weak password policies, insecure storage of credentials, and improper transmission.
- Compromised credentials can lead to unauthorized access, data breaches, identity theft, and financial fraud.
- Attackers can use stolen credentials to impersonate users, manipulate data, or launch further attacks on the system.

How QA Can Help:
- Advocate for strong password policies and Multi-Factor Authentication (MFA).
- Test how credentials are stored and transmitted.
- Keep up with the latest vulnerabilities and ensure your testing reflects real-world scenarios.
Inadequate Supply Chain Security: Failure to properly assess, secure, and manage the various components that make up the mobile app’s supply chain. Includes third-party libraries, SDKs, frameworks, and even the development tools used to build the app.
- A vulnerability in any component of the supply chain can compromise the security of the entire app.
- Attackers can exploit these vulnerabilities to inject malicious code, steal data, or gain unauthorized access.
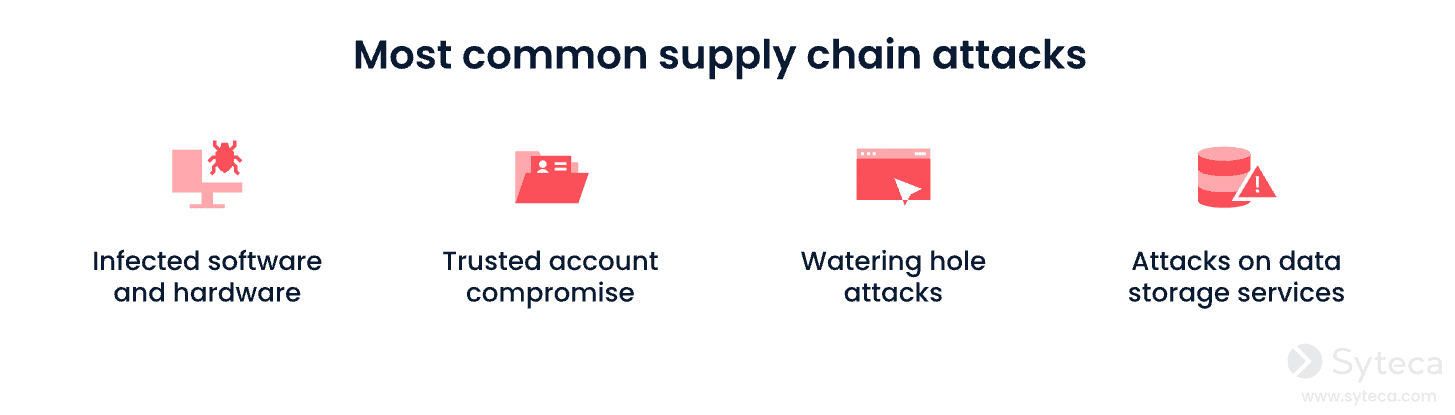
How QA Can Help:
- Maintain an inventory of all third-party components.
- Evaluate these components before integration and ensure they’re updated regularly.
- Work closely with developers to implement robust monitoring and vulnerability management processes.
Inadequate Privacy Controls: Failure to adequately protect user privacy within the mobile app. Includes collecting more data than necessary, not obtaining proper consent, storing sensitive data insecurely, or sharing data with third parties without user knowledge or permission.
- Violations of user privacy can lead to legal consequences.
- They can also damage user trust and the reputation of the app and its developer.
- Users may stop using the app or even take legal action if their privacy is violated.
How QA Can Help:
- Test how data is collected, stored, and shared within the app.
- Stay informed about privacy to ensure compliance.
Action Items for the QA Team
- Integrate Security Testing
Incorporate security testing into the software development lifecycle. Identify and address vulnerabilities during the early stages to minimize risks before release. - Invest in Training
Provide continuous training for QA engineers on the latest mobile security threats and solutions. Equip the team with knowledge of tools, techniques, and standards in cybersecurity. - Leverage Tools
Utilize mobile security testing frameworks like OWASP ZAP, MobSF, and QARK to automate and enhance testing efforts. These tools help identify vulnerabilities through static and dynamic analysis. - Collaborate with Developers
Work closely with developers to address security issues as they arise. Collaboration ensures security is embedded in the product from the ground up. - Stay Informed
Keep up-to-date with emerging security threats, trends, and vulnerabilities. Regularly review industry reports, attend seminars, and follow OWASP updates. - Add Non-Functional Security Test Cases
Extend the test suite to include security-related non-functional test cases. For example, validate secure data storage, enforce encryption standards, and test for input/output vulnerabilities.
Key Takeaways
By integrating security testing into the development process, collaborating closely with developers, and staying informed about emerging vulnerabilities, QA teams can help identify and address risks before they become serious issues. Staying up-to-date with the latest OWASP lists allows QA teams to address emerging risks effectively and incorporate the most current best practices. Through collaboration and continuous improvement, QA teams play a pivotal role in shaping a secure future for mobile applications.
Reading Time: 4 minutes
Don’t miss out the latestCommencis Thoughts and News.

Gülce Özbek
QA Engineer


